December 1, 2021: First Insecurity
In December 2021 several people, notably, Mr. 42, identified that the “Flat Earth Friend Finder” was completely open and did not require any authentication to view all the users positions on the globe.
Yes. The “Flat Earth” friend finder locates people on the globe. Proving that the app is a scam.
Videos by Mr. 42:
- Hacking the Flat Earth Friend Finder
- Hacking the Flat Earth Friend Finder, Part 2 (Thank you, David Weiss!)
Nearly 3 years ago David Weiss knew his app has serious security flaws. The web page revealed the location on the globe for EVERY user of the app. What did he do to patch the problem? He renamed the URL from “getUsersForMap” to “personalMappingInapp”. Did he do anything to the leaking of the user’s location on the globe? He did. The app now returns the entire user record. More on that later.
July 16, 2022
Bert Rickles noticed that the Friend Finder has severe problems leaking Private info in the app and published a video.
Decompiled Source Code
In July, 2024 the decompiled Android Application was distributed to many interested people. Unsurprisingly the “Flat Earth” app uses the globe for everything. Much hilarity ensued.
October 15, 2024: New Insecurity
Around the week of October 6 I was contacted by some white hat hackers. They had examined the source code and determined that the web server that the app communicated with was horribly insecure. They has attempted to communicate the insecurity to the support email address for the app, but the support email address didn’t exist so it bounced.
Based on the nearly 3 year history of cavalier security, the non-existent support email address, and the fact that the app is a scam, I decided to inform the world that the app was plagued with security problems.
What was wrong with the app? There existed an endpoint that served 100 user’s full data record. This endpoint required no authentication at all. Simply putting this URL in your web browser you would receive 100 user’s worth of:
- Location on the globe
- User ID
- Device ID
- Update date
- Creation date
- Country
- User Name
- Email address
- Password, in the clear
Someone promptly posted Dave’s own user data on X. It initially exposed Dave’s location and password. I asked for that data to be obscured so it was reposted with that info redacted. You’re welcome, Dave.
But, this wasn’t it. This was just the tip. The white hats informed me that there were several other vectors where the user data for all 200,000 users could be exfiltrated.
The previously hidden Google map showing all the users on the globe was revealed to be at the new address, “personalMappingInapp”.
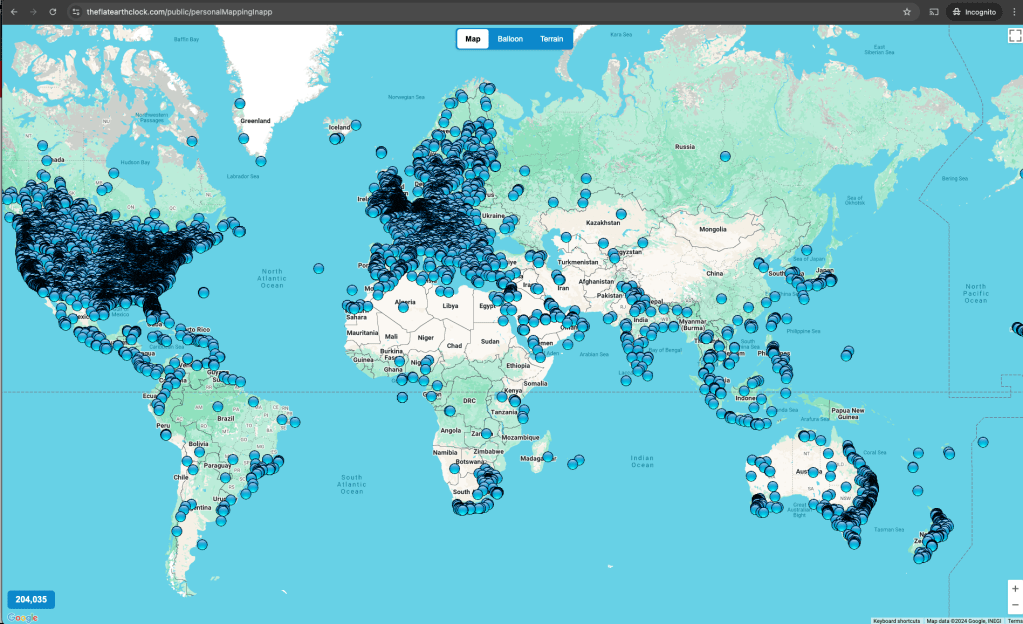
The location for every user that has ever launched the app with location enabled is pinpointed on the globe map. Seeing this is reserved for users that pay an additional annual fee. But it’s available for free.
It’s critical to note that this lists every user. Not just users that have opted in to the “Friend Finder” feature. This will be important later.
As of October 15, 2024 the Google Play Store description for the app claims that the app doesn’t store any data. But the application provably stores a large amount of data. This may be a direct violation or Europe’s GDPR laws.
David Weiss’s Response
When a breach is discovered, and especially when evidence is found of a previous breach, for example, noticing that a server has been leaking info for some time, the standard operating procedure for responsible reporting is to immediately make a statement asking people to be aware there was a breach.
Did David send his thanks for informing him of this massive insecurity? Did David Weiss immediately shut off the server leaking the data? Did David inform all his users that their data was potentially leaking? Did David hire a security team to do what he should have done 3 years ago and make sure the app was secure? No. He went on the attack and immediately started a cover up.
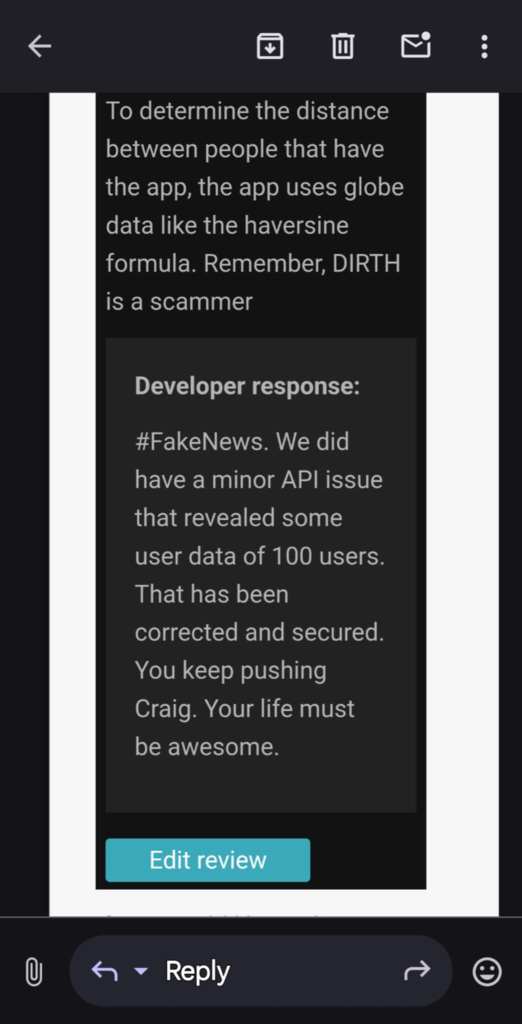
One user, Craig McNeil, known as FTFE on YouTube updated his review of the app on the Google Play Store. David called it a “minor API issue” and “#FakeNews”. While he wrote this the API was still able to be used to exfiltrate 100% of the end user’s data including passwords.
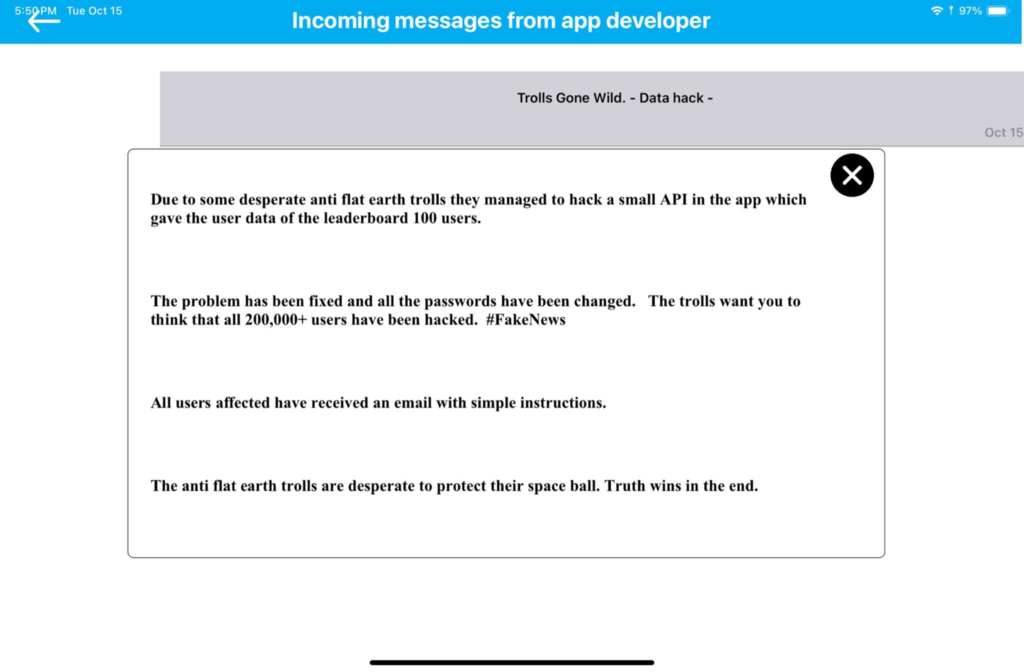
David did an in-app notification to all users claiming that only 100 users were affected, that they were informed, and that their passwords has been reset. Dave was covering up that all 200,000 user’s data was still viewable without authentication.
He attacked the people informing him calling them “anti-flat earth trolls”. Ironically signing his false message with “Truth wins in the end”.
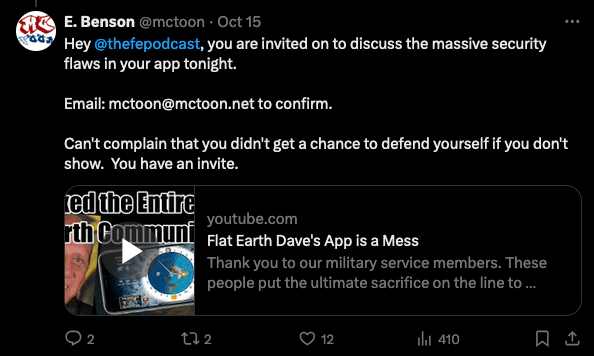
Meanwhile I was posting on X in response to David’s posts that the app was still insecure. Throughout the day I continued to let him know that his app was still insecure. Based on his coverup I decided to feature the leak in a live video that evening. I let him know that he was invited to defend his security flaws. He cannot say he didn’t get a chance.
Instead David Weiss attempted to scare my by sending a poorly constructed “Cease and desist” email. The same lies were in the email. Since I had seen the source code and was in contact with the white hats I knew this was a lie.
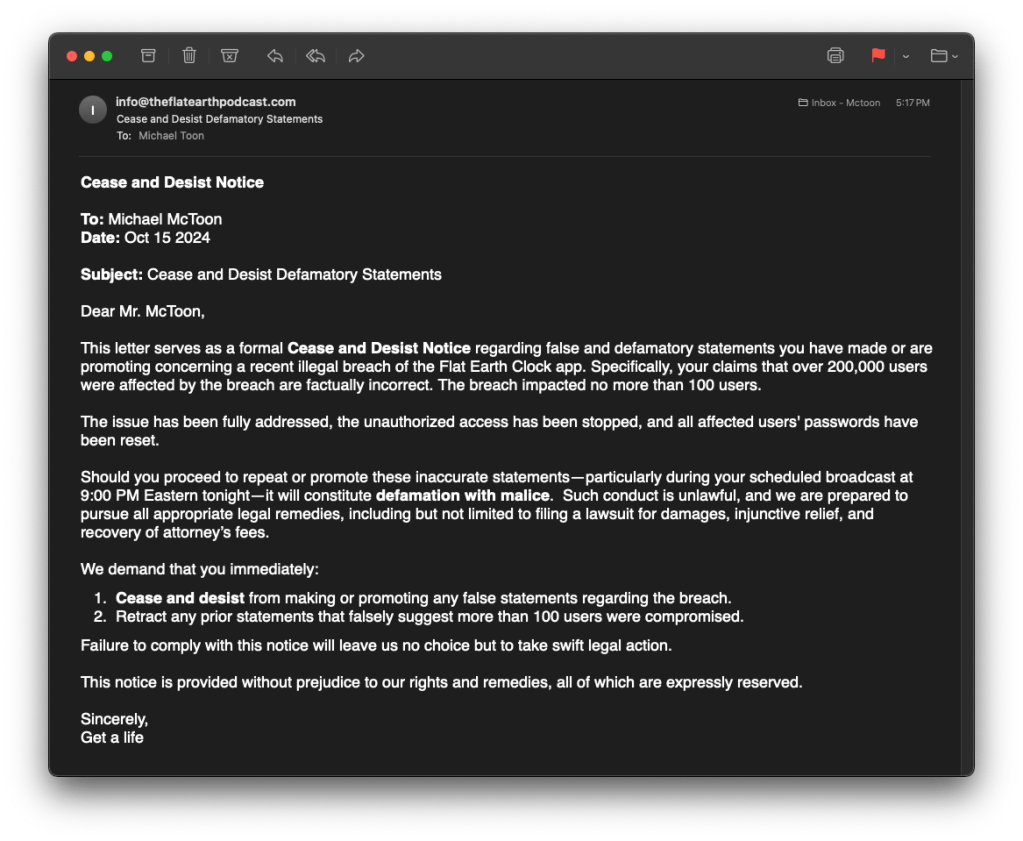
Since all the information I was sharing was factual, the cease and desist was ignored.
As a bonus Dave has informed me that he wishes to be called “Get a life” in the future.
October 16, 2024: More Coverup
People posted on X asking Dave if his app was still leaking all user data. He denied, calling it fake news.
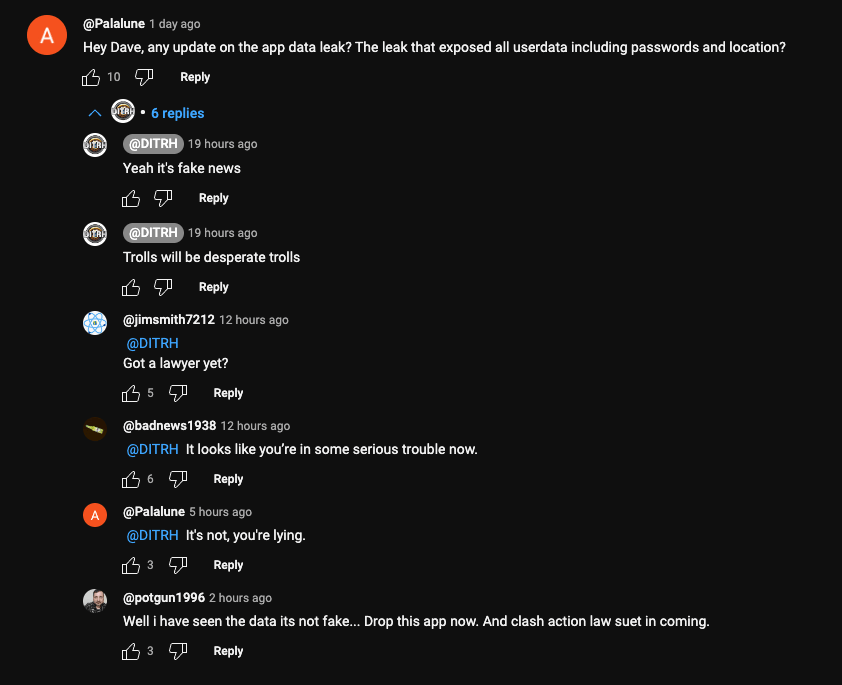
But people were still confirming that the API was still leaking data.

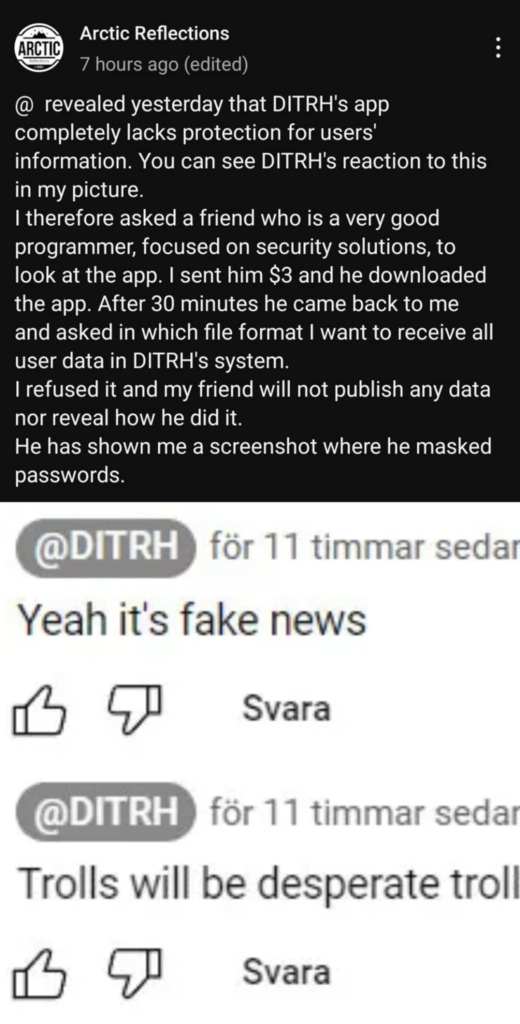
Dave once, again went on the attack and blamed others, while not fixing the leaks or at least shutting down the server leaking the data.

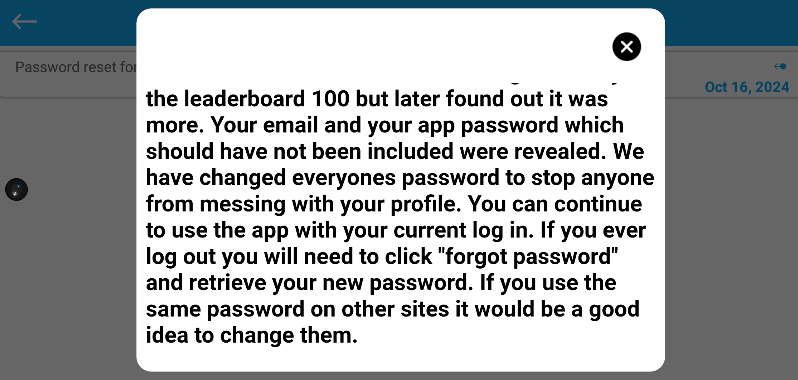
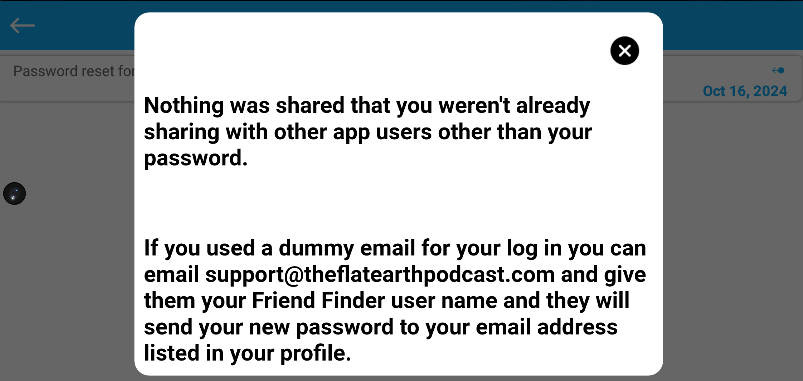
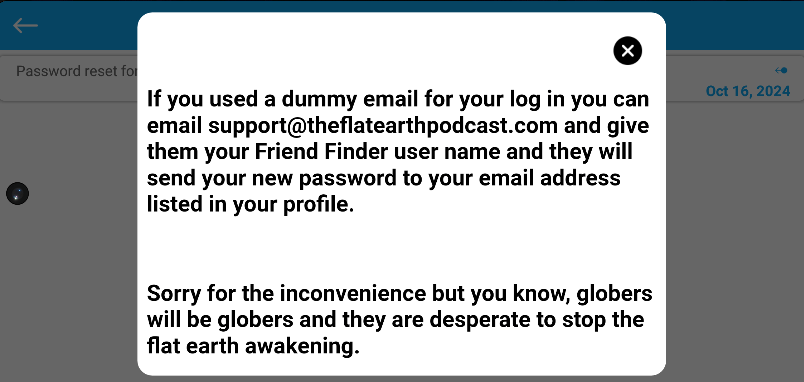

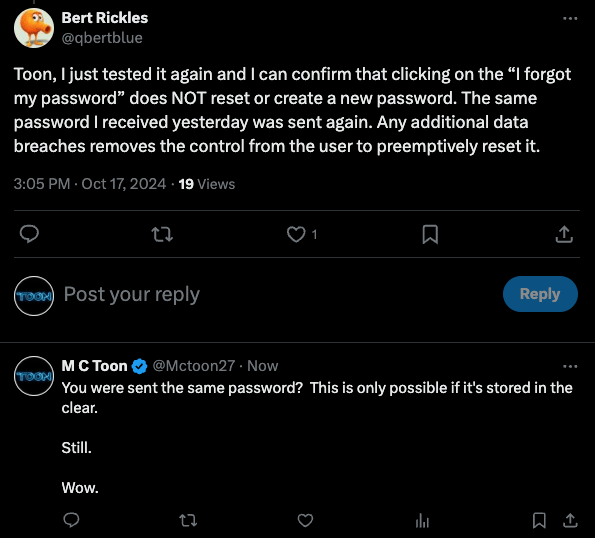
Proving that Dave has no interest in security he informs his users that they can email him and he will send them their new password. This is not a temporary password that the user will need to change later. At the time there is no password change feature in the App. This also suggests that the passwords are still stored in the clear, not hashed. A practice that was done away with decades ago because of security problems.
Critical information directly from the developer
On October 16 the developer informed the white hat that the passwords had been “encoded”. This is unusual verbiage. Passwords are “hashed”. The white hat asks how they are encoded and the developer refuses to answer responding with “So, you can hack it again”. This is very concerning. Properly hashed passwords cannot be hacked. That’s the point. An ideal answer would be “Over 200,000 rounds of PBKDF2-HMAC-SHA512”. Or something similar. Since libraries that do this are free and easy to use, there’s no reason not to use a state of the art high security solution. This would have been quite a flex. But, as we find out later, the developer chose the worst possible option.
October 17, 2024: Live Coverup on YouTube
Dave posted on X that he was going live with a Crypto currency podcast on YouTube. I let several people know and we popped in to the live chat. We started asking Dave about the data breach. He lied and covered up.
“We did have a data leak. Some hacker got in and got into one of our APIs and was able to extract everyone’s data—the data that they’re already sharing with every other user. However, they did get their passwords, so what we did is we changed everyone’s password, and we blocked the data leak. We’re actually just finishing up. They’re going to have a new version of the app out, um, maybe even later today. The whole thing is gone. It’s a nothing burger that the anti-flat Earth trolls are just freaking out over.” -David Weiss, on CryptoCafe – ep211, October 17, 2024
In reality, where the rest of us live, at that very moment the API was still open and data could be exfiltrated. Leaking private information for 200,000 users is not a “nothing burger”. This was not “data that they’re already sharing with every other user”. This was not users that opted in to the “friend Finder” feature, it’s all data from all users. This was data that users absolutely do not expect to be shared: street address, gender, sexual preference, email address, location on the globe, . A friend, MxXxD and myself emailed the show hosts and they invited us on the show. Dave IMMEDIATELY ran away. Refusing to even talk to anyone that can challenge his lies about flat earth. Much hilarity ensued.
Meanwhile, testing suggests that passwords are stored in the clear.
October 19, 2024: Developer’s Uncomfortable Request
While reporting vulnerabilities in the app both Dave Weiss and the developer made the white heat very uncomfortable. The developer demanded to know the white hat’s identity. No screenshots to share at the moment. The developer attempted to blame the white hat instead of accepting responsibility. This is not the way to behave when someone is giving you free advice on how to fix your garbage app.
October 20, 2024: Threat From Dave to the White Hat
The white hat, receives an email from Dave with a threat. Lawyers are called.
This is seriously bad. The threat is not veiled. The white hat has been providing free security advice. No more bug reports will be sent.
October 21, 2024:
Dave has claimed many times that the only people who have their location shared are the ones that have opted in to the Friend Finder, this is a premium add-on, probably a rather small subset of users opt in. Yet the number of users listed in on the globe map is a significant number. The application source code absolutely uploads the location for all users shortly after launch. Source code doesn’t lie, Dave does. This source code shows that the location is uploaded without first checking to see if the user is opted in to the friend finder:
How about hard proof? Certainly. Here is NASA’s Launch Pad 39A on the friend finder, notice there are no blue dots on near the launch pad.

One of the white hats then set their phone to a location near launch pad 39A. The very same launch pad where Apollo 11 launched from to put men on the moon. Then the white hat launched the flat earth app. Forcing GPS coordinates is easily done by a skilled hacker. No account was created, no permissions were granted within the FE Clock App to include the user in the friend finder. Still the app requested to share the location of the phone. Not having chosen to participate in the “Friend Finder” this user certainly should never have been included on the globe map. Yet, after launching the app, a new blue dot appears exactly where the white hat placed the GPS coordinates.
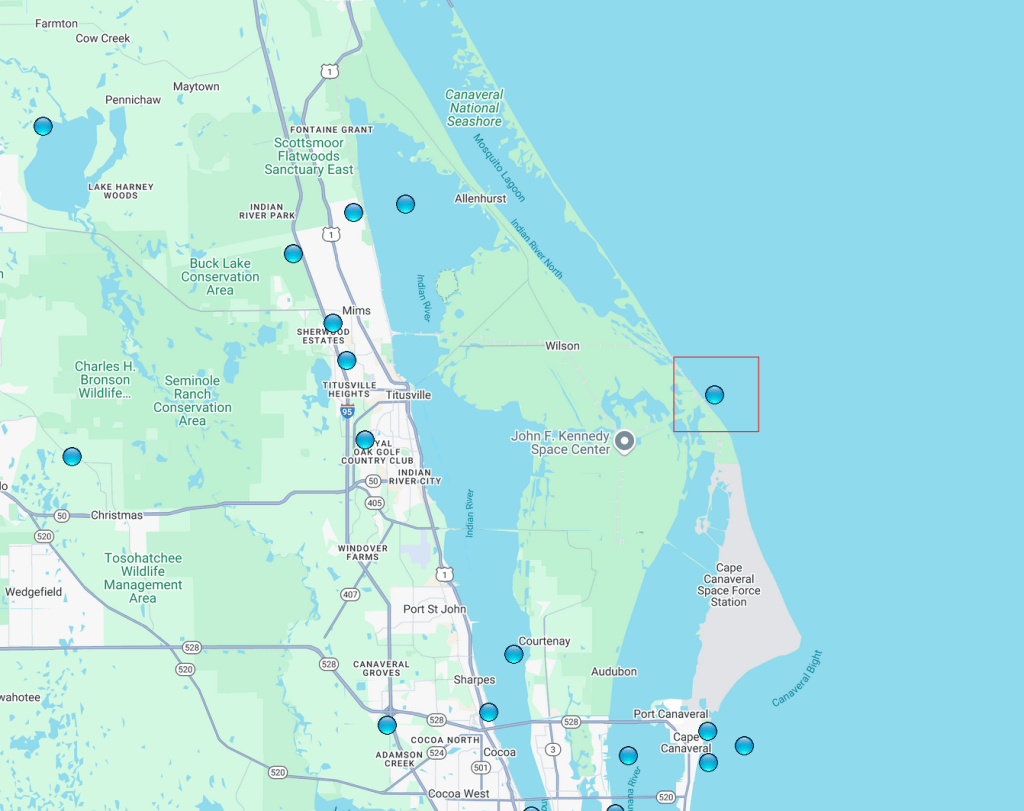
This proves, again, that David Weiss is lying when he claims that only people opted in to the friend finder have their location on the globe leaked.
What is the current status? The API is still up, still serving out private information and PASSWORDS IN THE CLEAR. User accounts can still be edited without authentication. Since Dave makes overt threats to the people that freely inform him of flaws in his application, he will not be informed.
October 22, 2024:
All data is still open. it’s important to keep in mind that this was not a “hacking” endeavor. Hacking entails interacting in some way with the application to put the system into an unusual state to leverage
What Can You Do?
Since Dave Weiss seems to have no intention to protect end user data, reporting his actions to the proper authorities is a great idea. This appears to be in violation of the GDPR rules so people in the EU might be able to report it. In the US each state has different requirements regarding breaches. If you are able, please report to the proper agency in the US.
If you are a security researcher, reach out to me via my contact page. I would love for this information to be more well known. There doesn’t appear to be any series of events where Dave will stop leaking PII. It seems that the application will need to be removed from Apple’s and Google’s app stores.